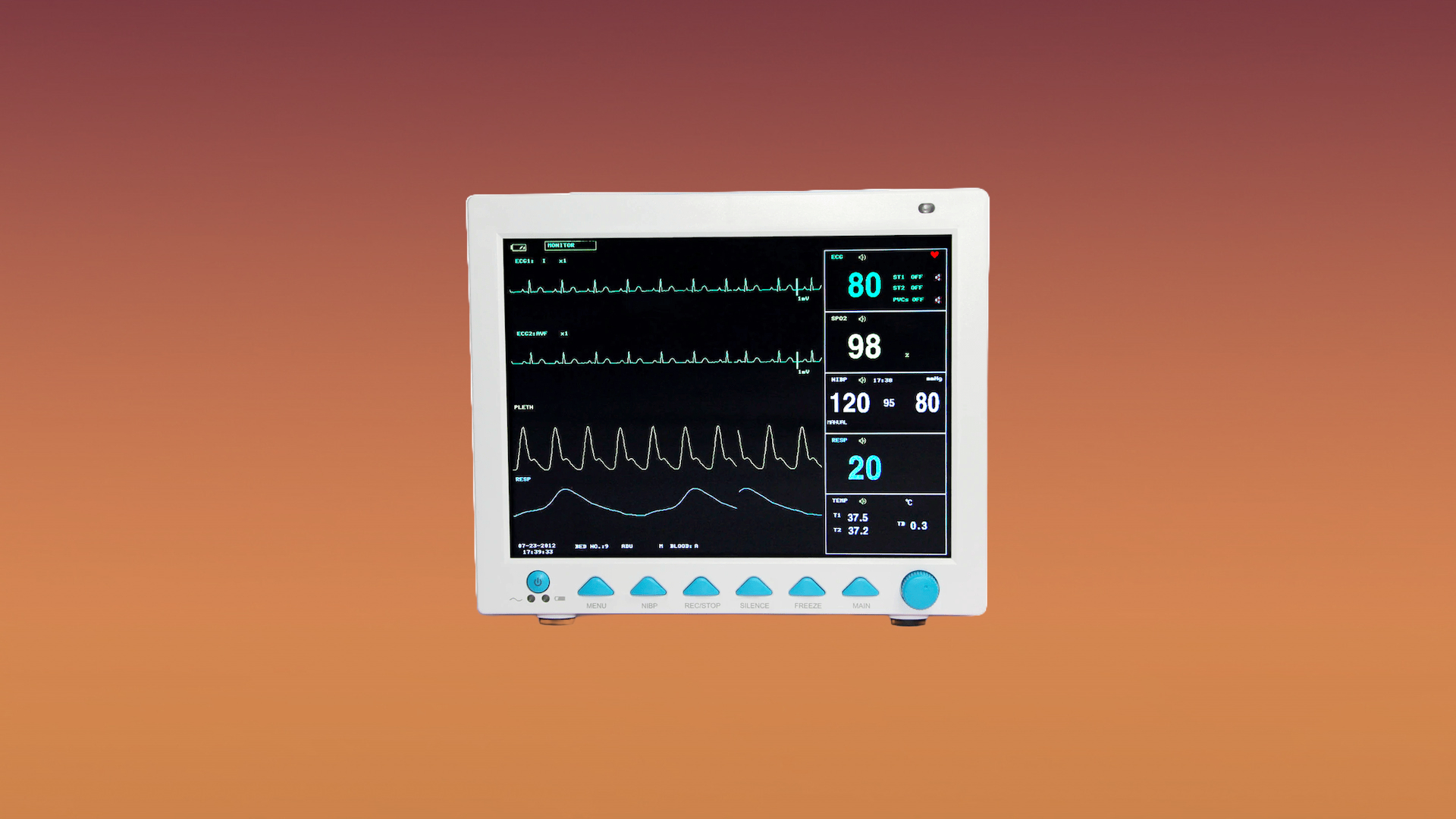
The US-based Cybersecurity & Infrastructure Security Agency recently released an investigation report involving three firmware versions used in a patient monitoring system called Contec CMS8000, used in hospitals and healthcare facilities. It was discovered that these devices had a backdoor with a hard-coded IP address, allowing the patient data to be transmitted. This is possible as the devices will enable a connection to a central monitoring system via a wired or wireless network, according to the product description.
The agency revealed the codes that transmit data to a particular IP address. This decoded data contains detailed information, such as the doctor’s name, patients, hospital department, admission date, date of birth, and other information about the people who used this device. This vulnerability is filed under CVE-2025-0626 with a CVSS v4 score of 7.7 out of 10. Two other vulnerabilities were filed under CVE-2024- 12248, which indicates that it could allow an attacker to write data remotely to execute a code, and CVE-2025-0683, which relates to privacy vulnerability.
“These cybersecurity vulnerabilities can allow unauthorized actors to bypass cybersecurity controls, gaining access to and potentially manipulating the device,” the FDA said, adding it’s “not aware of any cybersecurity incidents, injuries, or deaths related to these cybersecurity vulnerabilities at this time.”
The agency mentioned that Contec Medical Systems is a medical device manufacturer based in China whose products are in hospitals, clinics, and other healthcare facilities in the European Union and the United States. However, a quick search revealed that these can also be purchased via eBay for $599. These devices are also relabelled as Epsimed MN-120, according to the FDA. Contec is a major manufacturer of medical devices that are sold in over 130 countries and are FDA-approved. The CISA research team recently discovered this vulnerability as a part of its coordinated vulnerability disclosure process.
The agency mentions the IP address is not associated with any medical device manufacturer. Still, it is a third-party university, though it doesn’t mention the university, the IP address, or the country it is sending data to. The CISA also ruled out this coding was meant to be an alternative update system as it does not contain standard update procedures such as tracking updated versions or doing integrity checks. Instead, it has the remote file shared and transmitted to the IP address. As a solution for such a networked device, the FDA strongly recommends disconnecting the monitoring device from its network and monitoring the patient’s vital stats and physical condition.
Breach of Privacy and Confidential Information
The Contec CMS8000 explicitly monitors a patient’s vital signs while storing its data in great detail, including electrocardiogram, heart rate, blood oxygen, blood pressure, respiration rate, and many others. This will raise privacy concerns since the FDA released a notice implying that they and medical facilities are unaware of its purpose. According to the report, Contec has not addressed the matter yet and has not released any firmware to fix this.
Many networked devices have been reported to have vulnerabilities, not exclusively being from a Chinese-based company. However, given the key role of such devices, due diligence, checks, and disclosures will be vital. Even if the data is transmitted to the university irrespective of its location, and since the report implies neither the FDA nor the hospitals are aware of this backdoor, it violates the privacy of every patient and doctor, not limited to one region. There have been multiple cyber attacks from China since January and concerns involving TP-Link, which would naturally heighten the problem with these devices.
#Backdoor #uncovered #Chinamade #patient #monitors #Contec #CMS8000 #raises #questions #healthcare #device #security


